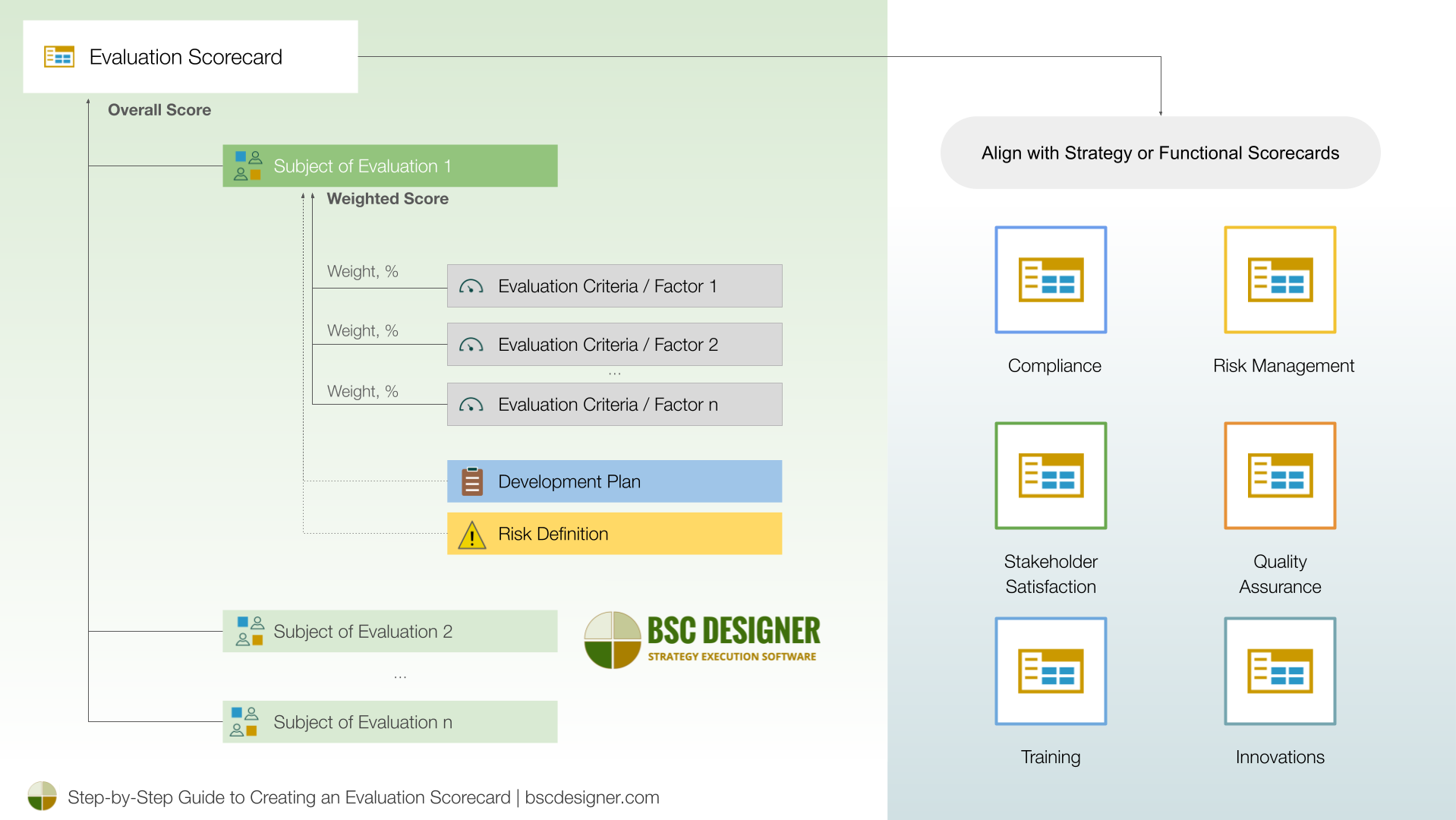
Third-party vendor validation has become an integral part of cybersecurity, procurement, compliance, and supply chain strategies. Previously, we discussed general practices behind the evaluation scorecard; in this article, we will discuss the creation of a vendor evaluation scorecard, using vendor risk management as an example.
We will demonstrate how to:
- Calculate the overall security score,
- Collect required evidence,
- Track security scores dynamically, and
- Align the results with other functional scorecards.
Define the Set of Evaluation Criteria
Follow current best practices to define the set of evaluation criteria for the vendor risk scorecard. This may include:
![]() Existence of a formal cybersecurity program
Existence of a formal cybersecurity program
![]() Implementation of multi-factor authentication
Implementation of multi-factor authentication
![]() Regular vulnerability testing
Regular vulnerability testing
![]() Adoption of the ‘Least Privilege’ practice
Adoption of the ‘Least Privilege’ practice
![]() SOC 2 compliance of the data center
SOC 2 compliance of the data center
![]() Data encryption in transit and at rest
Data encryption in transit and at rest
![]() Cybersecurity insurance
Cybersecurity insurance
![]() Intrusion prevention and detection systems
Intrusion prevention and detection systems
![]() Cybersecurity awareness training
Cybersecurity awareness training
![]() Data breaches reported
Data breaches reported
![]() The number of data breaches reported
The number of data breaches reported
Depending on the type of criteria, it can be configured as:
- Binary – with possible states “yes” or “no.”
- Quantitative (for example, measured in %) or qualitative (natural choice or Likert scale).
- Criteria can be optimized for maximization (like % of employees who passed cybersecurity awareness training) or minimization (like the number of data breaches).
Learn more about best practices for managing evaluation scorecard.
In BSC Designer:
- Switch to Strategy Workspace.
- Navigate to New > New Scorecard > More templates…
- Use the “Vendor Risk Management” scorecard template.
Assign Weight Depending on Risk Profiles
Weight the evaluation criteria according to the risk profile of the vendor.
For example:
- Vendors with access to sensitive information will have a high weight for criteria like “Cybersecurity Insurance” or “Data breaches reported,” while
- Vendors with no access to sensitive information will have a high weight for more common criteria like “Multi-factor Authentication” and implementation of the “Least Privilege” practice.
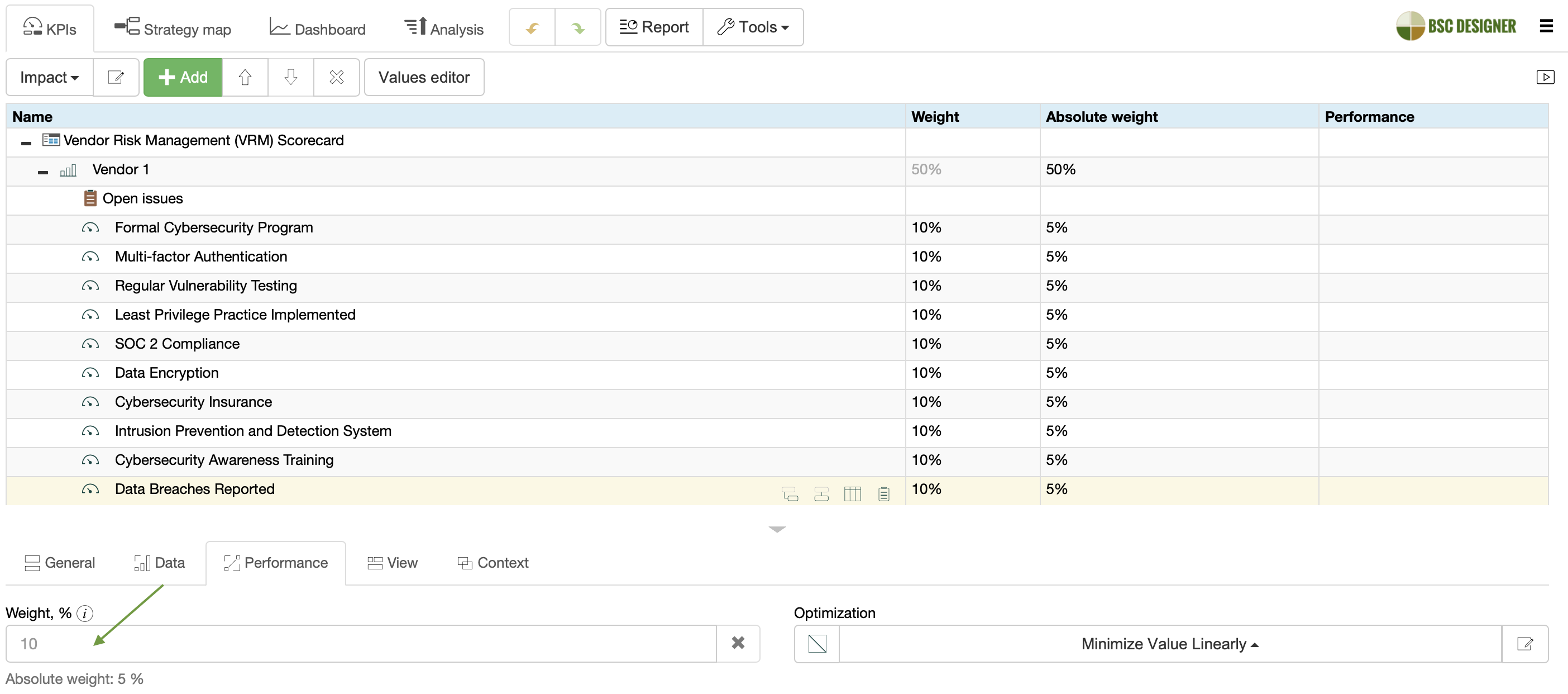
In BSC Designer:
- Select an evaluation criterion.
- Switch to the Performance tab.
- Adjust the relevant weight in the Weight property.
Build Hierarchy of Vendors
Group vendors into a hierarchy based on the vendor tier. Propagate evaluation criteria for each vendor.
In BSC Designer:
- Create groups using the “Add” button,
- Copy and paste a set of evaluation criteria into each group, and
- Rename the set name to match the vendor name.
Initiate Evaluation of Vendors
Assess vendors based on the evaluation criteria to identify relevant vulnerabilities.
- Enter evaluation scores manually into the scorecard or
- Import them from an Excel spreadsheet for self-assessment by the vendor.
Attach relevant evidence provided by the vendor, such as certifications and policies in practice.
In BSC Designer:
- Update scores manually via the Data tab.
- Use Tools > Export data to export evaluation criteria to Excel for the vendor’s self-assessment.
- Attach evidence to the evaluation criteria or to the mitigation plans articulated via the Initiatives dialog.
Continuous Risk Monitoring
Track changes in vendor evaluation scores over time, such as changes in relevant certifications or the number of data breaches.
- Define the revision period for each evaluation criterion
- Monitor issues relevant to the evaluation criteria.
- Plan for the improvement of vendor evaluation scores.
- Plan for vendor offboarding.
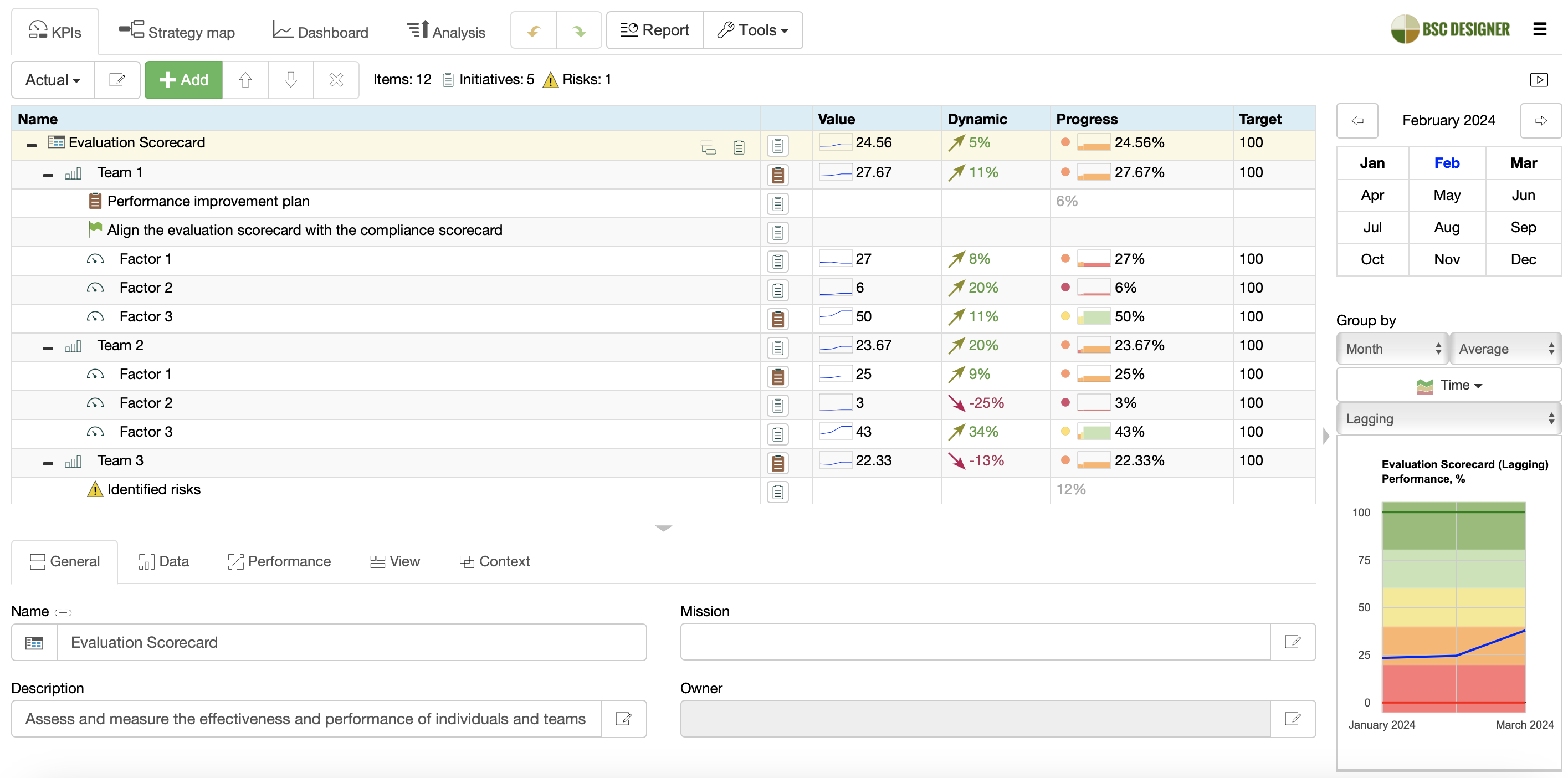
In BSC Designer:
- Setup Update Interval for an indicator via Values Editor
- Use Values Editor to assign scores to specific dates.
- Use Dynamic columns to see how the score changes over time.
- Use Initiatives to track data breaches and mitigation actions—update status and time span.
- Use comments for the score to track issues and Initiatives to map improvement plans.
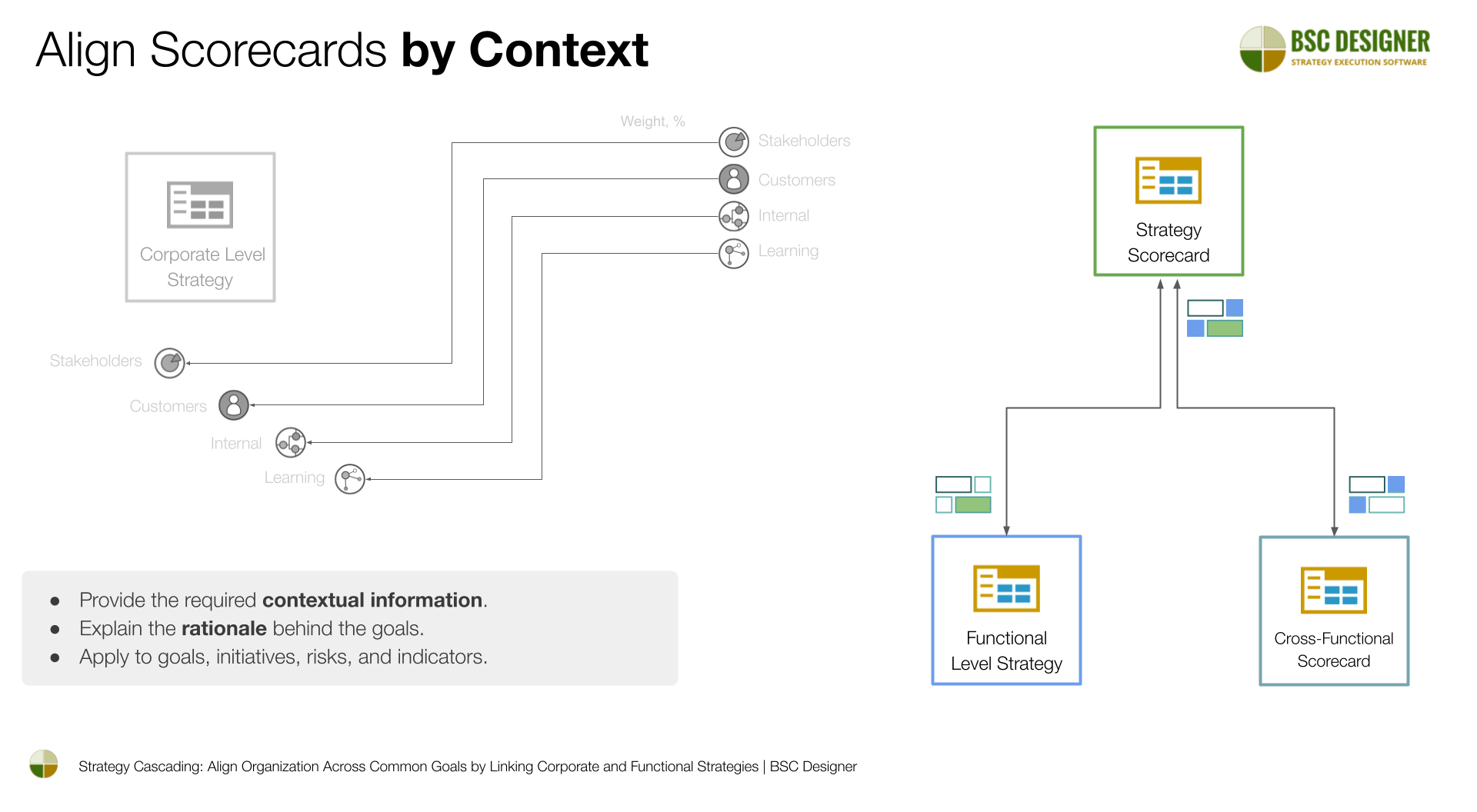
Alignment with Strategy
Align the vendor risk assessment scorecard with other strategy and function scorecards, such as governance or compliance scorecards.
- Use the overall risk score of the vendor portfolio.
- Use the risk scores of specific vendors.
- Cross link initiatives from various scorecards.
In BSC Designer:
- Copy the Vendor score item and Paste it into the relevant scorecard.
- Select the “Link by data” or “Link by context” option.
Conclusions
In this article, we discussed the steps to create a vendor risk management scorecard:
- Definition of evaluation criteria
- Assigning weights depending on the risk profile of the vendor
- Continuous risk monitoring
- Alignment of vendor risk score with other scorecards
Learn more about more specific mechanics of evaluation scorecards.
BSC Designer is strategy execution software that enhances strategy formulation and execution through tangible KPIs. Our proprietary strategy implementation system reflects our practical experience in the strategy domain.